If you don't like the idea of the feds or anyone else looking over your shoulder while you surf, there is new software that is free. It is Open Source software titled I2P. Wikipedia states:
All communication is end-to-end encrypted (in total there are four layers of encryption used when sending a message), and even the end points ("destinations") are cryptographic identifiers (essentially a pair of public keys), so that neither sender nor recipient of a message need to reveal their IP address to the other side or to third-party observers.
This is not the same process as using an anonymous server. That process routes your address through one server for a fee. The anonymous server owner can be compelled to reveal your address. I2P has no central server, but rather a uses a large network of users wherein no one is trusted. Your outgoing and incoming data is scattered in a random fashion across the network. It is also randomly redistributed on the fly. Email is similarly made anonymous through another utility that uses the same system.
The program is located at:
I2P Anonymous Network - I2P
All the wikipedia info is at I2P - Wikipedia, the free encyclopedia
I have installed it and it seems very reliable and it is easy to use. You will notice a drop in speed because so much data is being encrypted and sent in so many directions.
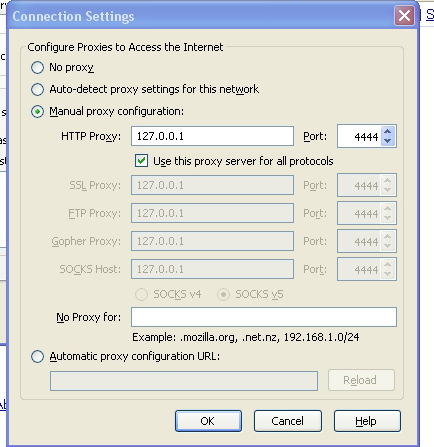
I use Firefox for my browser. All I had to do was change from automatic proxy to manual proxy. You can switch back and forth at will, with automatic revealing your address and manual not. I have attached a picture of that menu. You can see the manual address. My real address is purposely blank. The number and port in the manual entry are the ones you should use.
This program is a joint effort between a team of hackers known only by pseudonyms. I imagine it is a nightmare for government snoops. Even if every single user were pinpointed, no user has any idea what data has passed back and forth via his connection and the data that has passed is recorded nowhere. No user has any idea of the address or identity of any of the others. Even the people who wrote the software wouldn't know what data had passed.
The human mind is not capable of grasping the Universe. We are like a little child entering a huge library. The walls are covered to the ceilings with books in many different tongues. The child knows that someone must have written these books. It does not know who or how. It does not understand the languages in which they are written. But the child notes a definite plan in the arrangement of the books—-a mysterious order which it does not comprehend, but only dimly suspects. -- Albert Einstein
All communication is end-to-end encrypted (in total there are four layers of encryption used when sending a message), and even the end points ("destinations") are cryptographic identifiers (essentially a pair of public keys), so that neither sender nor recipient of a message need to reveal their IP address to the other side or to third-party observers.
This is not the same process as using an anonymous server. That process routes your address through one server for a fee. The anonymous server owner can be compelled to reveal your address. I2P has no central server, but rather a uses a large network of users wherein no one is trusted. Your outgoing and incoming data is scattered in a random fashion across the network. It is also randomly redistributed on the fly. Email is similarly made anonymous through another utility that uses the same system.
The program is located at:
I2P Anonymous Network - I2P
All the wikipedia info is at I2P - Wikipedia, the free encyclopedia
I have installed it and it seems very reliable and it is easy to use. You will notice a drop in speed because so much data is being encrypted and sent in so many directions.
I use Firefox for my browser. All I had to do was change from automatic proxy to manual proxy. You can switch back and forth at will, with automatic revealing your address and manual not. I have attached a picture of that menu. You can see the manual address. My real address is purposely blank. The number and port in the manual entry are the ones you should use.
This program is a joint effort between a team of hackers known only by pseudonyms. I imagine it is a nightmare for government snoops. Even if every single user were pinpointed, no user has any idea what data has passed back and forth via his connection and the data that has passed is recorded nowhere. No user has any idea of the address or identity of any of the others. Even the people who wrote the software wouldn't know what data had passed.
The human mind is not capable of grasping the Universe. We are like a little child entering a huge library. The walls are covered to the ceilings with books in many different tongues. The child knows that someone must have written these books. It does not know who or how. It does not understand the languages in which they are written. But the child notes a definite plan in the arrangement of the books—-a mysterious order which it does not comprehend, but only dimly suspects. -- Albert Einstein


 I agree.
I agree.